The lines that will follow will provide this article’s readers with some general information about one particularly noxious computer virus named .Combo Ransomware. The computer virus that we are currently discussing belongs to the cryptovirus category – this is a sort of Ransomware that’s got the ability to lock the user’s personal documents by employing a complex encryption code. As soon as the virus has carried out its insidious process, it uncovers itself by displaying a pop-up note – via this note, a ransom payment is requested. Feel free to leave a comment with your experience in remove the virus from your PC.
The goal of the notification pop-up is to give instructions to the virus’ victim regarding how to carry out the ransom payment and have it send the hacker who has infiltrated the computer system. In such a case, the cyber criminals would demand a ransom in return for a customized decryption code that is supposedly capable of unlocking your personal files. In case the required money doesn’t get paid, the victims are threatened to never regain access to their computer files again. In the event that the noxious .Combo Ransomware has already secured your documents and you’re seeking a solution for your problem, we suggest that you carry on with reading this article.
How .Combo Ransomware Works
Programs of the Ransomware class have little in common with other kinds of harmful software, which makes them a unique form of pc viruses. This is also one of the main elements which make Ransomware such a challenging and difficult to fight off form of computer malware. Unlike other harmful programs, like Trojans, Ransomware doesn’t usually get recognized and stopped by a good number of commonly employed security tools. It’s precisely the unique and uncommon approach of Ransomware that makes this malware virus so sneaky. Rather than attacking and seeking to inflict damage on your pc or data, .Combo Ransomware wouldn’t do any of this.
This way, the virus is able to remain concealed while locking-up your data files. The data encryption is, in reality, a frequently used data protection mechanism, which is usually regarded as harmless. Employed by the Ransomware, however, it may cause you big problems by preventing you from accessing your own documents and keeping them hostage for a ransom payment. Typically, such computer viruses are extremely stealthy and in most cases only some really subtle signs and symptoms of the virus’ actions are present which makes it that more difficult to spot such a virus before it’s too late.
Bitcoins and Payment
As soon as the file encryption of all the targeted files is over and the customer no longer has the ability to access their private files, the noxious software virus would move on to the final stage of its agenda – the blackmailing for a ransom. The way the Ransomware victim is notified about the money requirement is via a notification produced onto the victim’s PC screen which message provides them with instructions which explain the way the money ought to be transferred. More often than not, users get quite intimidated once they realize that their pc has been infiltrated by a Ransomware, which is precisely what the cyber-terrorists rely on.
The more worried the Ransomware victim becomes when they learn about what has been done to their private files, the bigger the likelihood that they’d give in to the internet criminal’s demands and issue the money transfer. But the truth is that this is exactly what you must not do. We highly recommend you have a look at all the potential options and take into account their positive and negative sides in order to make the right decision instead of right away transacting the ransom to the online-criminal. As an example, our Removal manual for .Combo Ransomware is one possible alternative option and though it may not always be totally successful in all cases, it is nonetheless still worth the go.
Prevention
Protecting your pc system against infections from viruses such as .Combo Ransomware is vital nowadays if you’d like your documents to be safe and accessible. The following paragraph will be very educational and useful for all the users who are trying to strengthen the overall protection and security of their PC and data. One very critical factor that may contribute to the subjection of your PC to potential hazards is what your online activities are and what online sites you typically open. Steering clear of shady and possibly dangerous online sites is essential if you seek to prevent cryptoviruses from getting inside your machine. Likewise, be cautious with all the internet junk messages that you could receive. It is widely known that all sorts of malware are often getting distributed through spam emails or harmful social network letters – this includes Ransomware as well.
In most cases, provided that you think that something you see on the internet appears possibly unsafe, you must not interact with it. The final tip we will give you in here would be to backup all valuable files that happen to be stored on your system and keep the back-up device disconnected from your PC if perhaps you suspect that your computer might be infected with Ransomware. This way, a Ransomware attack to your PC will probably be just a mere annoyance!
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
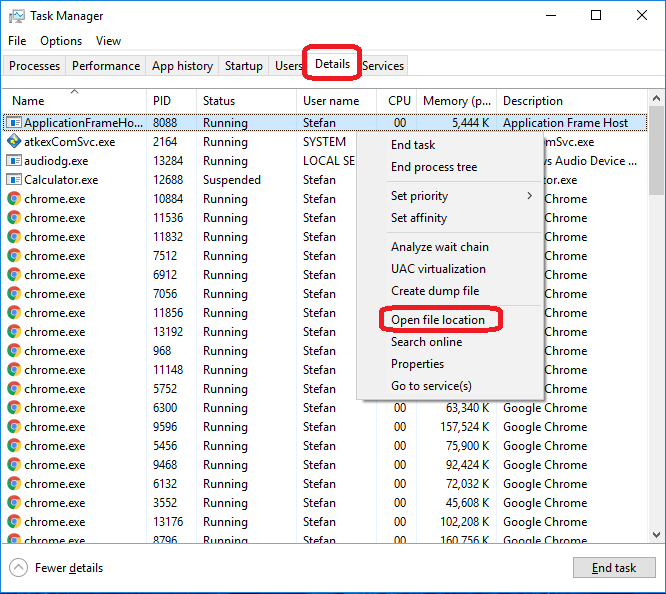
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: The Hosts file
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.
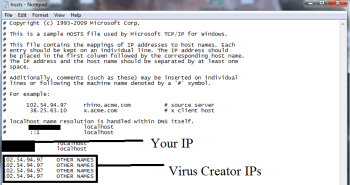
If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the virus.
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:
If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious, disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: Decryption
The previous steps were all aimed at removing the Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them.

Leave a Comment