A new ransomware strain has been defiantly hitting computers on a large scale over the past few days. While the majority of infected users are currently in Germany, the attack surface appears to be expanding with rampant rapidity. It’s unclear at this point which cybercriminal syndicate is responsible for these compromises, but the trojan’s operation evidently reflects the worst practices of digital extortion. What happens is the victims’ personal files become encrypted, and their names turn into a gibberish sequence of 32 numbers and characters followed by the .locky extension. The targeted operating system identifies these items as LOCKY files that cannot be opened no matter what software the user may resort to.
 Original files replaced by weird-looking .locky items in a folder
Original files replaced by weird-looking .locky items in a folder
This onslaught is also characterized by a number of distinctive attributes other than the disgusting file skewing. The ransomware changes the affected user’s desktop wallpaper to a warning message, whose text is reiterated in files named _Locky_recover_instructions.txt. It’s plural because the aforementioned TXT document can be found inside every single folder holding locked items that used to be the victim’s personal data. These are essentially ransom payment instructions that shed light on what happened to the files and provide a walkthrough regarding recovery options.
In particular, the message says:
“!!! Important information !!!! All of your files are encrypted with RSA-2048 and AES-128 ciphers. Decrypting of your files is only possible with the private key and decrypt program, which is on our secret server.”
In a nutshell, this means that the .locky file extension virus harnesses asymmetric cryptography to encrypt file contents and also employs symmetric cipher to encode filenames proper.
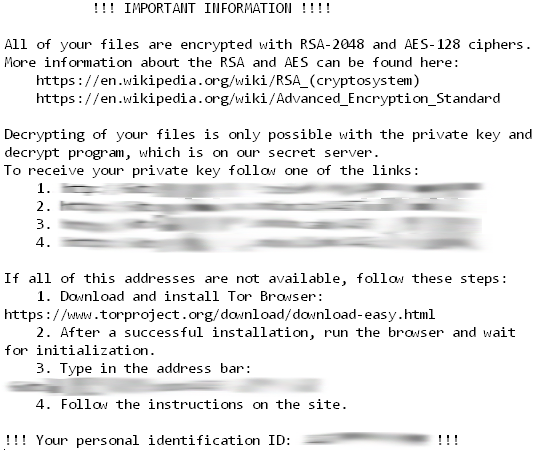 Contents of the _Locky_recover_instructions.txt file
Contents of the _Locky_recover_instructions.txt file
As a result, the victim can neither open his or her pictures, documents and videos nor even determine which entry stands for which file on the hard drive. At that point, the extortionists recommend a ‘panacea’, which is claimed to be capable of decoding everything in exchange for a fee. It’s called the Locky Decrypter. In order to use this tool, the plagued person needs to visit a Tor gateway specified in the _Locky_recover_instructions.txt file and submit 0.5 BTC to a Bitcoin address indicated on the page. The use of The Onion Router technology and the payment workflow over cryptocurrency are the precautions that the offenders adopt to stay anonymous and get around law enforcement. Unfortunately, most of these exactors manage to stay on the loose and keep coining new breeds of ransomware.
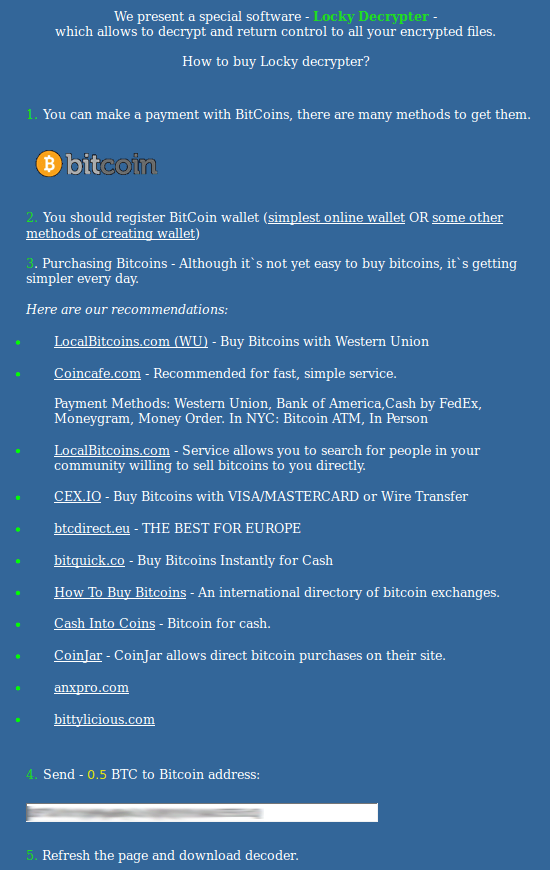
Locky Decrypter purchase guidance tailored by the scammers
Locky Decrypter purchase guidance tailored by the scammers
Propagation of the .locky virus relies on a social engineering hoax. In particular, prior to being infected, most people have received harmful email messages titled “ATTN: Invoice J-68522931” (the 8 digits may vary). These emails pretend to be invoices from General Mills, but they aren’t. The attached Microsoft Word document is the object that executes the ransomware as soon as the unsuspecting user opens it. Exploit kits, which generally pose a more sophisticated mode of contamination, are not involved in the .locky campaign for the time being.
It’s not a good idea to pay the ransom and purchase the Locky Decrypter program. This is what the cybercriminals insist on, but it’s certain not in any affected user’s interest. Since this ransomware may fail to disable the Volume Shadow Copy Service on the machine, it makes sense to apply a couple of smart techniques in order to recover the encrypted data.
Remove *.locky file extension virus with automatic cleaner
This is an exclusively efficient method for taking care of malware overall and ransomware threats in particular. The use of a reputable security suite ensures scrupulous detection of all virus components and a complete removal thereof in a single click. Be advised, though, that uninstalling this infection and recovering your files are two different things, but the need to remove the pest is indisputable as it has been reported to promote other Trojans while operating.
-
- Download and install .locky file virus removal software. Having launched the solution, hit Start Computer Scan button
- The tool will come up with scan results, reporting the detected malware. Select the Fix Threats option to remove all the infections that were found. This will lead to complete extermination of the virus under consideration.
Get encrypted *.locky files back
It has been mentioned that .locky extension malware applies strong crypto to render files inaccessible, so there’s no magic wand that restores all of the encrypted data in the blink of an eye, except of course submitting the unthinkable ransom. There do exist techniques, though, which can lend you a helping hand in recovering the important stuff – learn what those are.
Automatic file recovery software
It’s kind of interesting to know that the infection erases the original files in an unencrypted form. It’s the copies that undergo the ransomware’s crypto processing. So tools like Data Recovery Pro can restore the deleted objects even if they got removed in a secure way. This workaround is definitely worthwhile as it proved to be fairly effective.
Shadow Volume Copies
This approach relies on the native Windows backup of files on the computer, which is conducted at each restore point. There is an important condition to this method: it works if the System Restore feature was toggled on before the contamination. Also, if changes were made to a file after the most recent restore point, they won’t be reflected in the recovered file version.
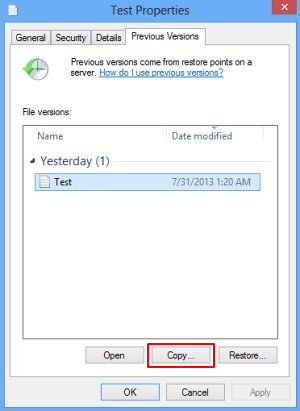
- Use Previous Versions featureThe Properties dialog for random files has a tab called Previous Versions. That’s where the backed up versions are displayed and can be recovered from. So right-click on a file, go to Properties, hit the above-mentioned tab and select the Copy or Restore option, depending on the location you would like it recovered to.
- Apply ShadowExplorerThe above process can be automated with a tool called Shadow Explorer. It basically does the same thing (retrieving Shadow Volume Copies), but in a more convenient way. So download and install the application, run it and browse to files and folders whose previous versions you wish to be restored. To get the job done, right-click on any of the entries and select the Export feature.

Backups
Out of all the options that aren’t ransom-related, this one is the most optimal. In the event you had been backing up your information to an external server before the ransomware hit your PC, restoring the files encrypted by this ransomware is as simple as logging into the respective interface, selecting the right files and initiating the restore transaction proper. Before you do so, however, be sure to completely remove the ransomware from your computer.
Check for possible remnants of .locky file extension virus
In case you chose to stick to the manual cleanup technique, some fragments of the ransomware may have stayed as obfuscated objects in the operating system or registry entries. To make sure there are no malicious components of the threat left, have your computer scanned with a reliable malware security suite.

Leave a Comment