Different cybercrime rings that coin ransomware have started vying for tech superiority in their illegal moneymaking business. Some of the newer breeds of these infections, for instance, are deploying two-step crypto, where a cipher routine is leveraged for file contents and then for the generated decrypt keys. Furthermore, a number of active samples are tweaking filenames along with the data proper. As the extortionists are permanently advancing in terms of the code sophistication, the latest ransom trojan known as Cerber has also made one step ahead. Its authors have built an audio interaction feature into the malicious solution, meaning that the victims can literally listen to the ransom alert and thus learn the black hat hackers’ demands.
This digital malady badly mutilates the infected user’s most important files. It encrypts them with AES standard and then makes sure the decrypt key is nowhere to be found on the plagued workstation. Meanwhile, the ransomware also replaces filenames with strings of 10 digits and characters and concatenates the .cerber extension to each one, making a random item look similar to �?su5cTyepkh.cerber’. All folders with encrypted files inside them are complemented with a triad of auxiliary documents titled # DECRYPT MY FILES #.html, # DECRYPT MY FILES #.txt and # DECRYPT MY FILES #.vbs. The last one in the array is a VBScript that produces a sound output when the user opens it.
The ransom instructions read “Your documents, photos, databases and other important files have been encrypted!” This fragment is followed by a listing of several steps to recover the locked data, specifically a recommendation to download and install the Tor browser, launch it, visit a personal web page with the .onion domain identifier, and follow further directions on the linked-to Cerber Decryptor site. The latter tells the victim to send 1.24 BTC, which is a little more than 500 USD, to a specified Bitcoin address so that the decryptor becomes available to download. The page also contains a time countdown script that displays the amount of time left before the ransom becomes twice as large, the deadline being 7 days.
Cerber is distributed on a Ransomware as a Service basis. The full code for this infection is available on a number of underground hacker forums, where interested parties can get it on condition that the creator will be subsequently earning a part of the revenue obtained from ransoms. Since there are different affiliates, the virus propagation channels may be diverse and range from spam all the way to exploit kits.
Ultimately, the only way to disrupt this firmly established scheme is to abstain from paying the ransom, which may be an unsuitable option because personal files are important. This is why ransomware workarounds are gaining relevance. Learn a couple of techniques to restore .cerber files and not pay a penny to the scammers.
Remove Cerber ransomware with automatic cleaner
This is an exclusively efficient method for taking care of malware overall and ransomware threats in particular. The use of a reputable security suite ensures scrupulous detection of all virus components and a complete removal thereof in a single click. Be advised, though, that uninstalling this infection and recovering your files are two different things, but the need to remove the pest is indisputable as it has been reported to promote other Trojans while operating.
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
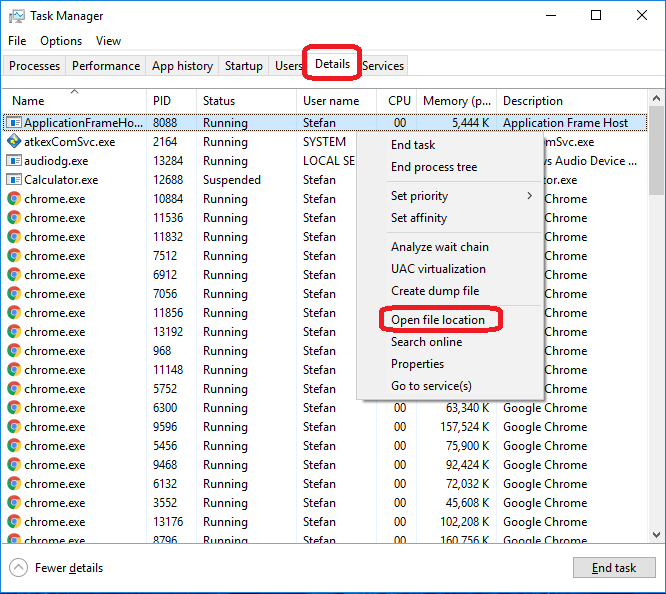
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: The Hosts file
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.
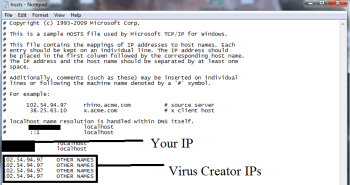
If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the virus.
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:
If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious, disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: Decryption
The previous steps were all aimed at removing the Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them.

Leave a Comment